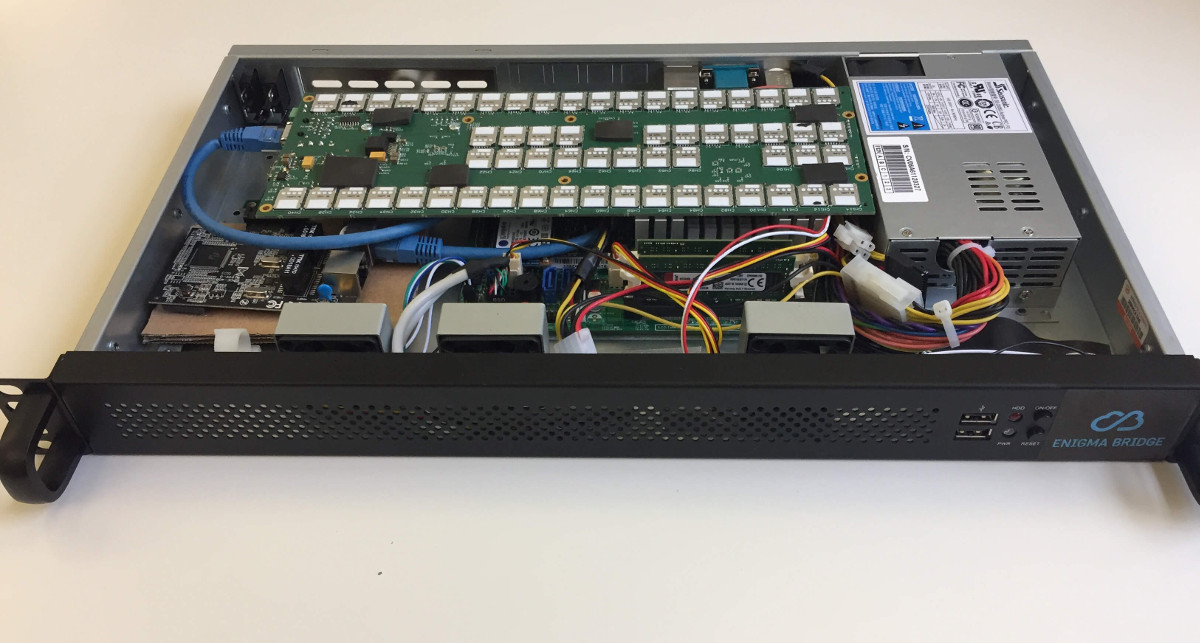
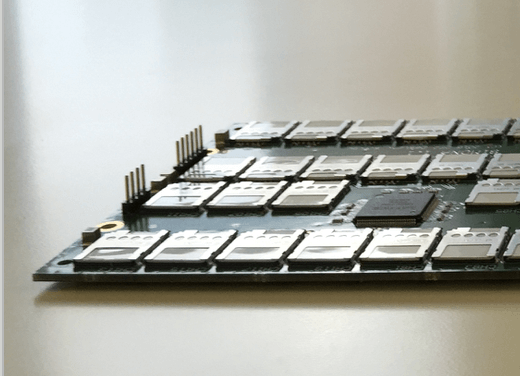
SIMONA - Smart Card Platform
A scalable platform for connecting Smart Cards
SIMONA board is a modern, scalable, and reliable platform for connecting large numbers of smart cards to host systems.
It adds minimum time overhead when running on full capacity.
What is hardware security
Smart cards and HSMs
When you talk to hardware security and compliance, people usually have in minde large, purpose-built appliances, requiring 24x7 support and developers who know how to use their complicated application interface.
Another option is to use smart cards. They have the same security evalutions, while the real security is likely to be better than that of HSMs. They have simple application interface. What they lack is a reliable infrastructure.
Enigma Bridge has changed that. We developed a reliable infrastructure and built a scalable cloud encryption service, where users are assigned their own smart cards.
Virtual hardware security - Enigma Bridge
Enigma Bridge uses smart cards as trusted secure processors for its cloud service. While smart cards introduce certain transaction latency, we can more than compensate this disadvantage in our cloud service.
Large numbers of small secure processors allows us to provide “virtualised” hardware encryption as customers get as many hardware resources as they need and when they need them.
-
Use of large number of smart cards means that each user can have their own secure processors when needed.
-
Dynamic allocation of smart cards to users makes the cloud service flexible, and scalable.
-
Increasing total hardware resources provides more resources to all customers at the same time, just like with common virtual platforms.
-
We can add custom code inside secure hardware when used as internal instances.
SIMONA - specification
-
Size: 280mm x 100mm
-
Communication interface: 1x RJ45, 1Gbps
-
Power supply: 12V from internal server PSU
-
Smartcards: 120, micro-SIM, we recommend use one type of smart cards
-
Software interface: low-level protocol description, examples in Python, Java smartcardio library
-
Other: 1.8V signalization of smart card activity
Availability
List prices:
- SIMONA board, no smart cards: $2,500
- SIMONA board & host server: starting at $3,200
Smart cards: NXP, Gemalto - get in touch regarding particular requirements
Delivery: 6 weeks lead time

Hardware Security Pros and Costs
Easiest way to demonstrate security
Everyone trusts their own software applications because, well - they are ours and we “know” we got them right. The issue is how to make others trust our applications, especially if the sole purpose of those applications is to protect data.
Security validations and how to conduct them is one of the problems with no simple solution. Secure hardware has been the main answer for more than 20 years.
Problem of Demonstrating Security
We can make it easier for others to verify quality and security of IT products or applications. We can define a clean application interface (API), separate the critical computer code into smaller modules that are easier to analyse, or show paths of sensitive data.
-
clean and simple application interface (API)
-
separate critical functionality into small software modules
-
define data flows through the product or application
Once we can define a clear interface and physically separate everything inside this boundary, it is possible to limit the scope of analysis of what is happening inside. Whatever happens, the data will remain inside and will not get compromised. This is why use of dedicated security hardware is far superior to software solutions.
Cost of Secure Hardware
The problem is that use of secure hardware involves hardware devices, which someone has to host, manage, replace, … manage. The use of these devices is not for light-hearted either. One has to have an extensive experience to use them correctly. One also has to have a budget to buy or rent them.
The Enigma Bridge technology solves the cost problem. The service is multi-tenancy while still physically separating user secrets. It features a native web service API and an enrolment process that can be fully automated.
Enigma Bridge has developed an innovative capability providing powerful, resilient, scalable and comprehensive cryptographic functionality
Steve Marshall, Former Head of Security Architecture at Barclaycard
Independent Security Benchmarks
While there is no perfect solution for verifying security, the best current benchmark is an independent validation of the quality of a product or application. In terms of security, there are currently two main standards.
FIPS140-2
Cryptographic Product Security Standard
Federal Information Processing Standard (FIPS) 140-2 - implemented by National Instituted of Standards and Technology (NIST), a US government agency, to validate security of cryptographic products.
A successful validation results in compliance with:
Level 1 - lowest level of security
Level 2 - shows evidence of tampering (hosting provider detects)
Level 3 - responds to attempts at physical access (users detect)
Level 4 - highest level of security
Common Criteria (CC)
Computer Security Certification Standard
An international standard, where compliance is demonstrated by national authorities in Canada, US, UK, Germany, and Spain
A successful validation results in an assurance level (EAL):
EAL1, EAL2 - functionally tested, structurally tested
EAL3 - methodically tested and checked
EAL4 - methodically designed, tested, and reviewed
EAL5 - semiformally designed and tested
EAL6 - semiformally verified designed and tested
EAL7 - formally verified designed and tested