Payment Processing In Cloud
Protect your payment system against cyber threats

Payment processing is moving to the cloud. We can see companies being dragged by PCI compliance and their current use of secure hardware (HSMs).
Enigma Payments offers PCI compliant protection of credit card numbers (PAN) and customer PINs. Simplify your deployment, de-risk encryption by using Enigma Payments managed service.
Enigma Payments
Tokenisation
Enigma Payments service offers several types of tokenization mechanisms.
If you build a new solution or can change your database schema, we can provide cryptographically strong reversible as well as irreversible tokenisation.
If your aim is to preserve the database structure, we can offer PCI-compliant format-preserving tokenization. (PCI Security Standards Council: Tokenization Product Security Guidelines v.1.0).
PIN Re-encryption
Chip&PIN transactions require the payment processor to re-encrypt PINs received from its terminals under the key of an acquirer.
Enigma Bridge Payments implement the DUKPT protocol as well as PIN (encrypted PIN block) re-wrapping.
All these functions are available through our web service RESTful API.
PAN Protection
Enigma Bridge Payments can provide a key, which browsers use to encrypt a credit card number before it leaves customer’s computer.
A single transaction then re-encrypts the credit card number from a transport to a database key so that payment processors database never contains a PAN.
Managed Service
Enigma Bridge provides Enigma Payments as a managed service so you don’t need to think about secure hardware or hardware appliances any more.
Simple Integration
All functions are available with RESTful API, which is easy to integrate. We also provide light-weight client libraries for Javascript, Java, and Python.
Scalable
Our service features high performance elasticity to handle short-time transaction peaks, as well as gradual growth of transactions as your customers grow.
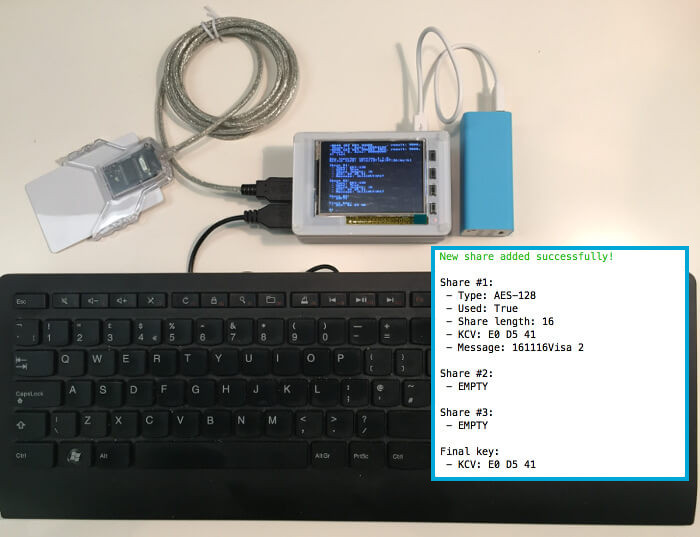
Remote Key Loading
Handling of third-party keys is the most complicated tasks for payment processors. Acquirers assume the payment processors are responsible for security of those keys as well as liable for costs of any security incidents.
Enigma Payments supports dual control / four-eye ceremonies for secure entry of plaintext key components. Once a key is entered into a secure hardware, it is wrapped for secure import into Enigma Bridge servers. Keys are ready for use immediately upon their import.