Virtual Hardware Encryption
Hardware security with virtualised hardware
Protect your data in the cloud and on-premise with our unique API. The API backed by trusted secure hardware processors or software engines. Strong foundations and flexibility for data control.
The API simplicity ensures that your business complies with data protection laws, including the coming EU’s general data protection regulation (GDPR). Short time to market, security as a service.
“The Enigma Bridge solution enables the straight-forward deployment and management of cryptography within business applications."
Steve Marshall
Former Head of Security Architecture at Barclaycard

Control Data and Applications
Control to comply, simplify, scale
Compliance, control and reporting - real-time and regular reports of access to data and use of applications.
Short time-to-market by removing the complexity of data control.
Total cost of ownership delivered as managed service.
Management
We protect, control the use, and safely handle keys to your data. Fully managed service provides flexibility and easy use.
Control and reporting
Powerful visualization and reporting features. Visualization of data use improve your control of data and applications.
Clean API
Integration tools hide all expert configuration. Developers just use data control and protection functions as any other business funtion.
Lock & key
Any cloud service needs physical security to equal on-premise systems. We use special-purpose hardware from leading vendors.
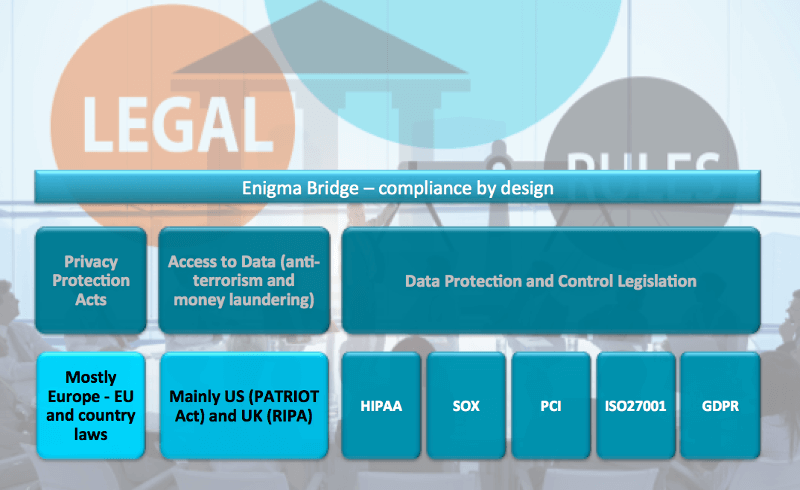
Stay On Top Of Regulation
Data protection is here to stay for a reason
Data protection legal framework is expanding. European Union introduces GDPR that applies to all who offer services EU citizens and handle their data. Regardless of where your company is based, you will have to comply with this regulation from May 2018.
Enigma Bridge significantly simplifies compliance by its design: traceability of usage and access to data, logging, controlling physical location of secrets, bootstrapping recovery processes.
Learn more about a revolutionary multi-party encryption we developed with University College London
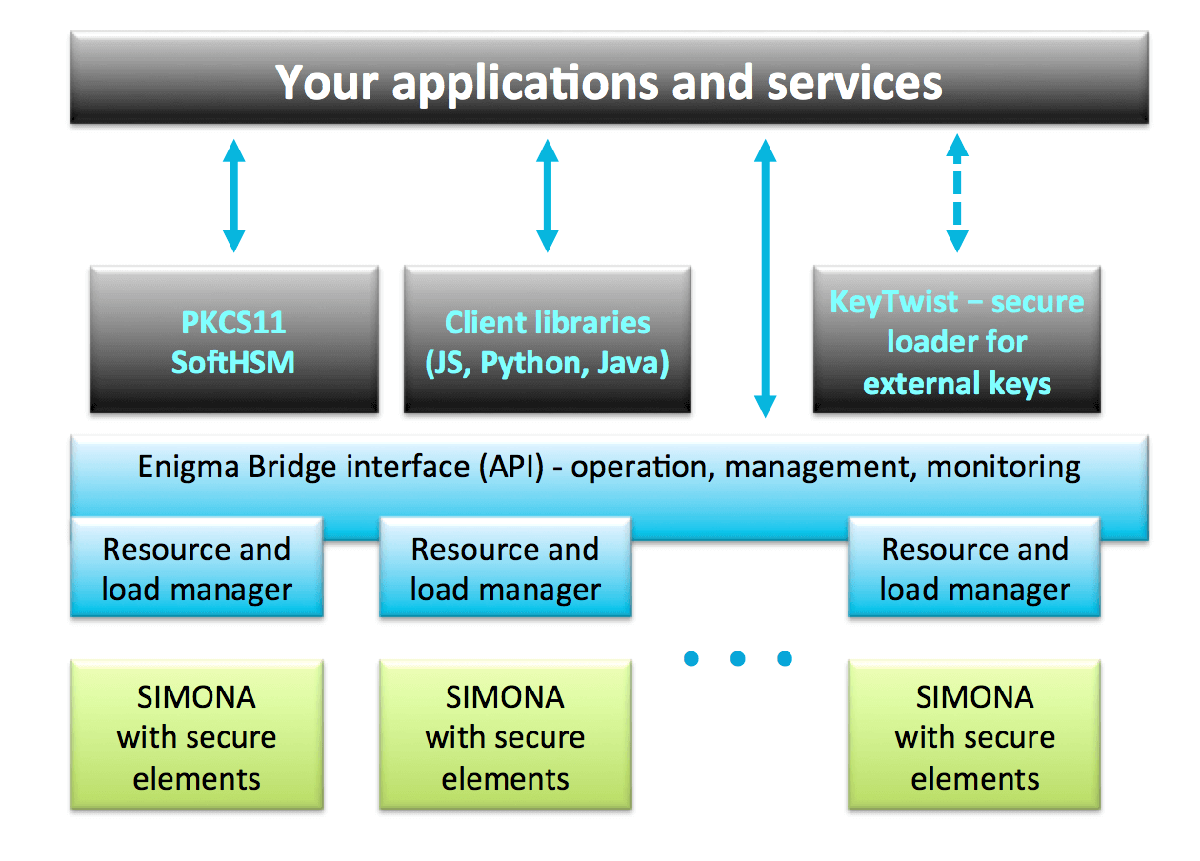
Enigma Bridge platform
Universal encryption service
Your applications can use directly our API, or one of the language bindings, or simply a PKCS11 library for transparent connection to secure elements provided by our platform.
Throughput and scalability
The platform provides multi-tenancy to optimize the resource utilization. Whether you choose own or shared security domain, you can grow it as your demand increases.
Simple, remote enrolment
You simply choose a template that fits your needs. We provide a range of templates, which simplify enrolment, as well as security audits. Encryption as a service.
How It Works
Simplicity
We are very proud on the architecture of our cloud service. It hides all the complexity of cryptography, load distribution, and resource management behind a simple application interface, a RESTful API.
Once you register your application, there is only one API function “Process Data”. It takes two parameters:
- handle to your user object inside the encryption service,
- data you want to process (authenticate, sign, tokenize, …).
Do you need legacy support? We have a PKCS11 library!
Security and trust
Special purpose processors protect your secrets. They connect directly to your cloud applications - there is nothing, no one in between. The HTTPS channel provides the second layer of encryption.
These secure processors are used by millions of users and applications. They have been designed to protect data in the most sensitive applications. They feature independent security evaluations (FIPS140-2 Level 3, EAL5+) providing ultimate physical security - your lock and key in the cloud.
Users of mobile or cloud applications
Apps using Enigma Bridge
End-to-end encryption to hardware CloudHSMs.
Secure internet connection

HTTPS to Enigma Bridge servers.
Enigma Bridge security domain

Network balancing, failover.
Enigma Bridge server

Work distribution, allocation of CloudHSMs.
Secure hardware element

Processing of client requests in CloudHSMs.
How you can use our API

Encrypt and sign
Basic operations you need to protect your data in transit and in your database.

Card number security
Functions you need are tokenization (incl. format preserving). As well as re-encryption from transport to storage. Yes, it is PCI compliant.
Authentication
The API has functions to create users, verify and reset their passwords, as well as to show failed tries.

Key management
We provide two main functions for flexibility and security. First you get an encrypted key. The second function reveals the key when needed.
See our API at work

EnigmaLink - secure file transfer
Use your Google drive to share files securely. The encryption uses three different keys - triple lock - for maximum security.

Key management - PKI
Encryption is nothing without key management. We’ve simplified key management. Launch your own certification authority in minutes. Including physical storage of keys in secure hardware.

Private Space - company VPN
Lorem ipsum dolor sit amet, adipiscing elit Aenean commodo ligula eget.

Strong Research Background
Secure web sites leak information
Enigma Bridge has extended the award winning research of Petr Svenda, our co-founder. He showed that all https keys leaked information about their origin.
“this is seriously awesome work” - Greg Linares, research engineer at Eeye Digital Security
This fact escaped experts for 30 years. It means that all companies are exposing a part of their security architecture and management processes online.
Meet our team
We are a group of skilled and experienced security and payments individuals.






