BlackHat USA, 2017
OPENCRYPTO: Unchaining The Javacard Ecosystem
PDF of talk slides
dedicated web site
https://backdoortolerance.org/
DEFCON 25
Trojan-tolerant Hardware & Supply Chain Security in Practice
PDF of talk slides
page about hardware
https://enigmabridge.com/hsm
Enigma Bridge & University College London
Demonstrations as shown at DEFCON25
Geo-distribution of control
Multi-party keys and encryption can be split between several computing platforms, implementations of operating systems as well as between geo-graphical locations.
This demonstration shows processors in 2 locations - at DEFCON and in our Cambridge, UK office.
Speeding-up encryption
Our hardware for efficient use of JavaCards makes large numbers of processors available to internet users without any visible bottleneck.
It also shows that the encryption protocol is fast for most of business use cases.
Attack resiliency
The last demonstration shows how your keys remain secure even when several of your processors may be compromised.
While we demonstrate this resiliency on decryption with three processors, we are efficient for much larger numbers.
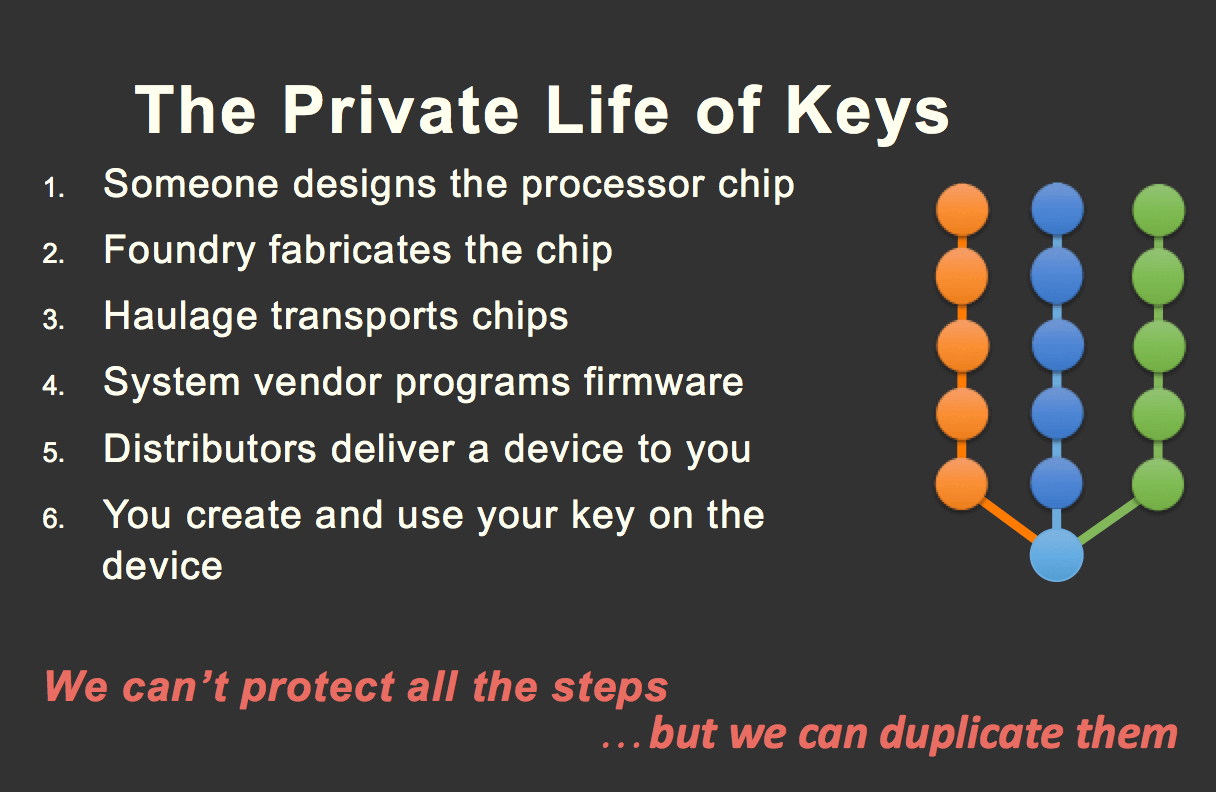
The Private Life of Encryption Keys
No-one tells you that security of your keys starts well before you create them
It is common sense but we tend to look at things in a certain way. We discuss security of cloud platforms, but forget they run on physical processors that had to be designed, manufactured, and initialized.
Payment industry may require hardware security modules (HSM) but they only protect your keys from people using them. What about people who manufactured their processors or network cards.
Building blocks of our solution
Diverse hardware platforms running Java
- Independent design
- Independent fabrication and disjoint supply chains
- Programmable
- Affordable and available
Javacards
Distributed encryption protocols
- No single trusted party
- Full and perfect distribution of secrets and keys
- Parallelised dstributed processing
- Provably secure (i.e, mathematical proofs)
UCL designed MPC protocols

SIMONA - Javacards via TCP/IP
Unique solution to integrate smartcards with cloud
Maximum speed access without bottlenecks
Over 100Mbps combined speed to Javacards
Control thousands of Javacards from your laptop
Developed by Enigma Bridge
Learn more / Order
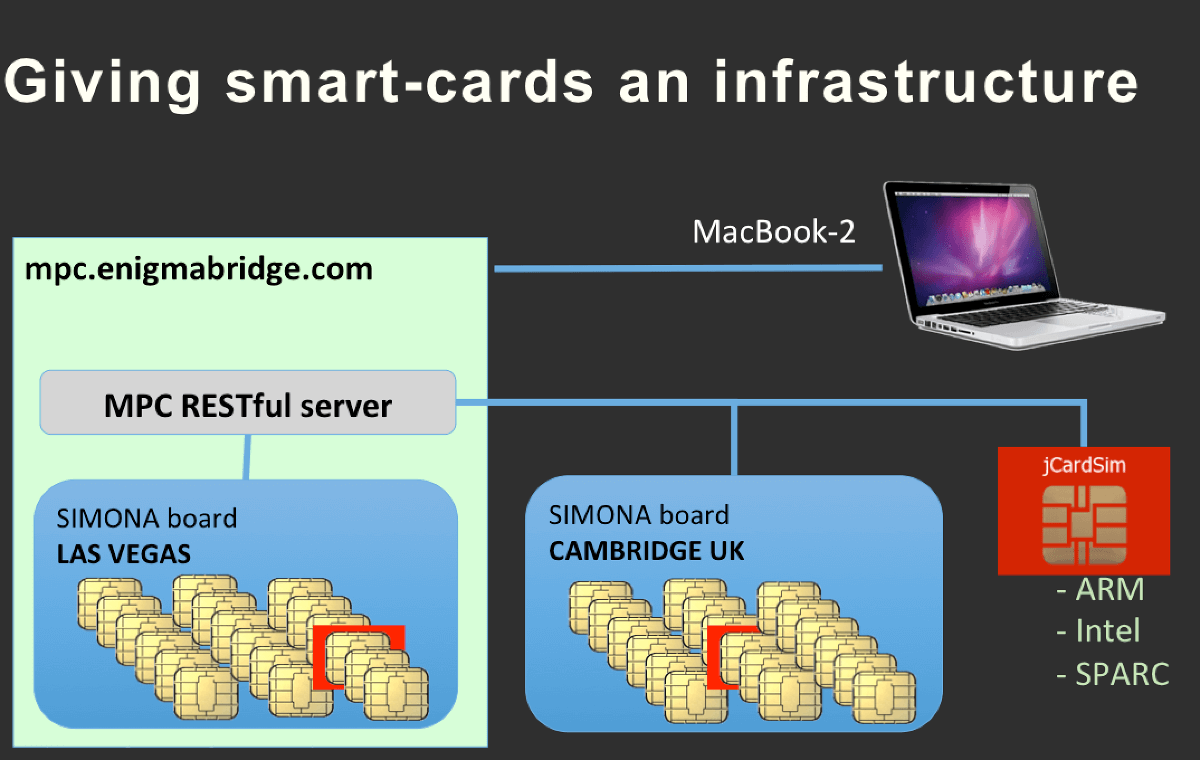
Giving smartcards an infrastructure
Encryption across platforms and continents
Use different Javacards designed and manufactured by independent parties
Run the same protocols in Javacard simulator on ARM, Intel, or SPARC platforms
Create keys distributed across countries and continents
Our distributed encryption is practical
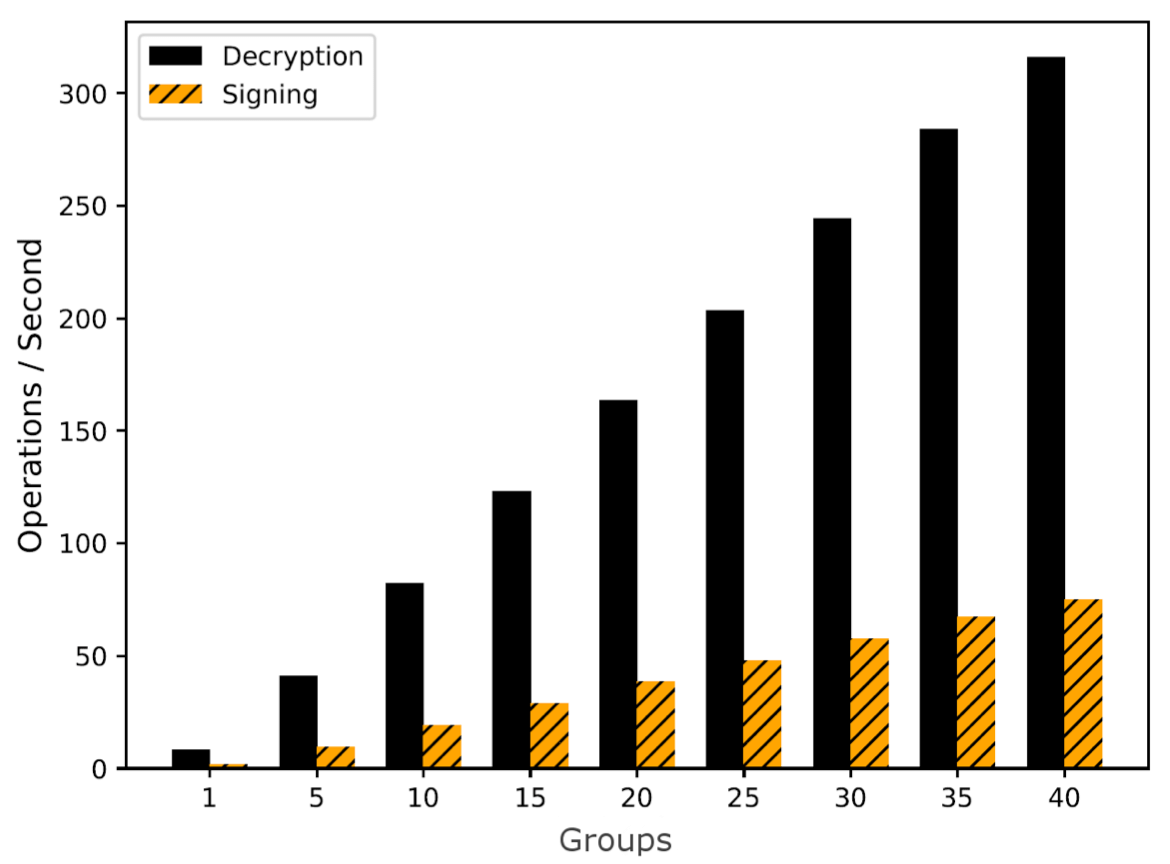
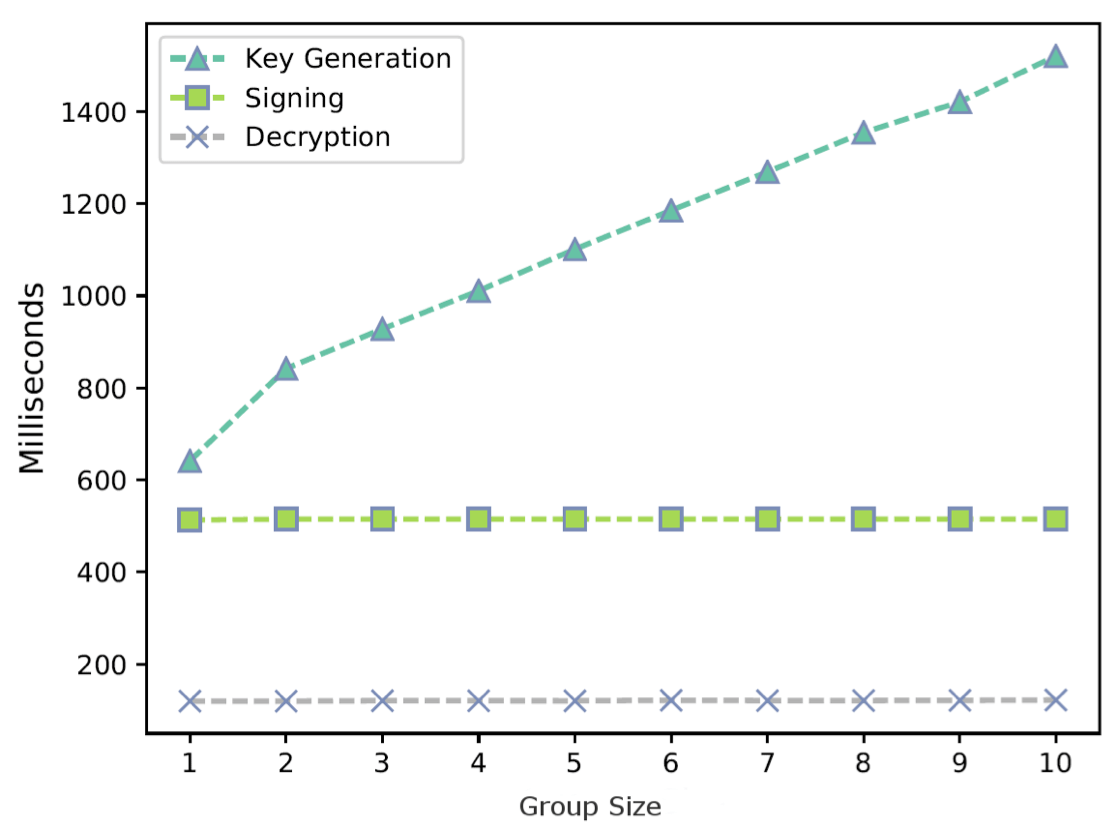
If Technology Fails, There’s Distrust
Use processors from different geo-political regions
Advances of countries in Asia, South America, and North Africa mean that we can use processors with diverse supply chains.
If there are bugs or malicous code in all such processors, we can still assume our security holds as long as world powers are not willing to share their secrets.