Secure Websites Leak Information
HTTPS/TLS protocol used by all secure websites points at vulnerabilities. It leaks sensitive information about cyber security management and can help hackers or government agencies extract sensitive data.
"It's striking that despite 30 odd years of cryptographic research
and security conferences, no-one noticed this problem
– which has been in plain sight all along."
Ross Anderson, professor of security engineering at the University of Cambridge
Until now, it has been widely believed that use of HTTPS:// on web sites does not provide any sensitive information that would endanger the security of the web service. No one expected that it could leak internal information about security management.
I am puzzled why people are not all over this - enormous implications. I discussed it in my organization yesterday.
Daniel Bilar - Information Security Specialist at VISA
This work on fingerprinting the software that generated RSA keys (from public keys!) is a must read.
Co-founder of CBX Group, co-founder of TrueCrypt audit project.
Our co-founder, Petr Svenda, released a paper on his team's discovery that https public keys leak information on how they were generated at USENIX Security Symposium and it received the best paper award. Their suprising results imply that freely available public encryption keys can put companies at risk. This public information provides details on their cybersecurity management, which to date has been considered a safe secret.
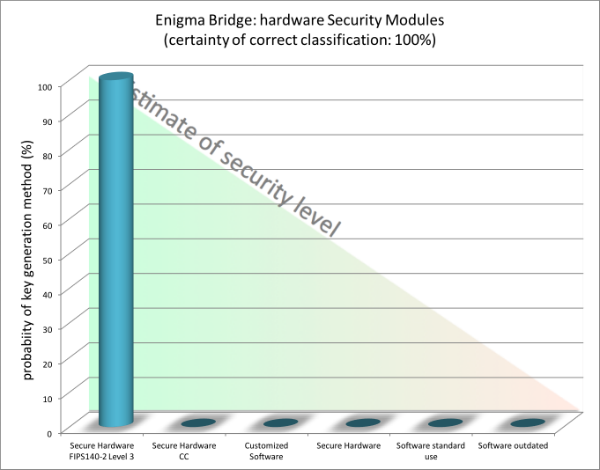
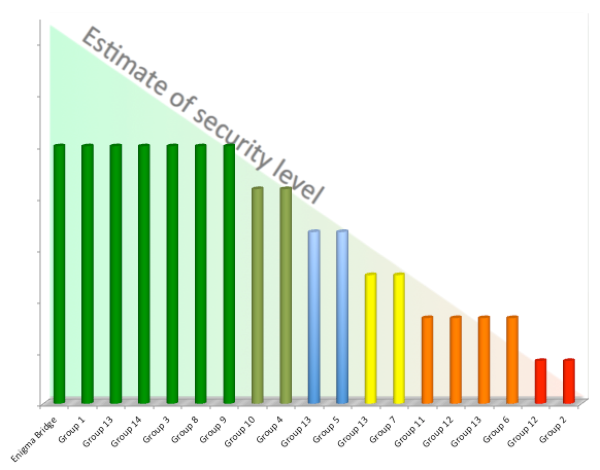
Our own key generation mechanism
See above how our scanning techniques can with 100% probabilty tell how our own key generation mechanism is constructed as well as some of the classification.
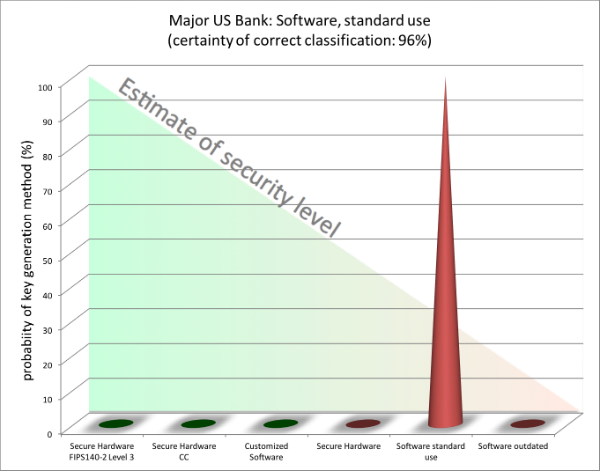
Example 1 - Major US bank
Whilst we neither want to reveal the name nor the exact key mechanism used by this major US bank, we can by scanning their system tell with 96% probability how their key management is setup. We’ve notified them.
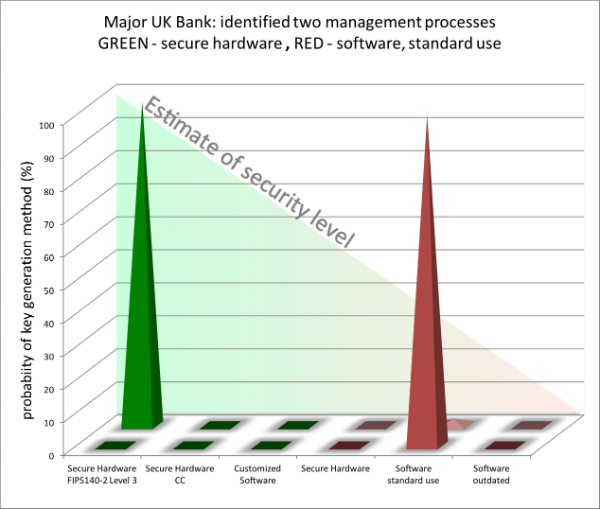
Example 2 - Major UK bank
Whilst we neither want to reveal the name nor the exact key mechanism used by this major UK bank, we can by scanning their system tell with 98% and 100% probability (respectively) how their key management is setup. We’ve notified them.
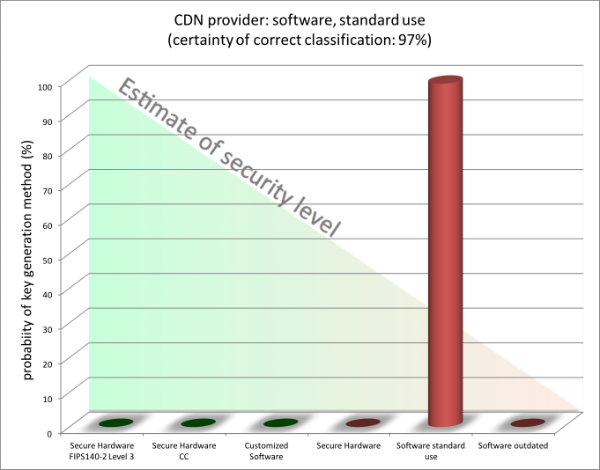
Example 3 - CDN provider
Whilst we neither want to reveal the name nor the exact key mechanism used by this major CDN provider, we can by scanning their system tell with 97% probability how their key management is setup. We’ve notified them.
In cyber security we trust…some of us at least
With all the breaches, cyber attacks and government snooping, companies are rapidly stepping up their cyber security defences. Key management is one of the major aspects of cyber security and keys generated and stored in secure hardware are proven to be more secure than those generated by software and stored in computer memory. Enigma bridge has brought to market Hardware-Seurity-as-a-service (Cloud HSM), allowing companies to protect their assets and users in a simple and cost effective way.